Netstat shows tcp6 on ipv4 only host
Why netstat shows tcp6 sockets even though you only have ipv4 configured.
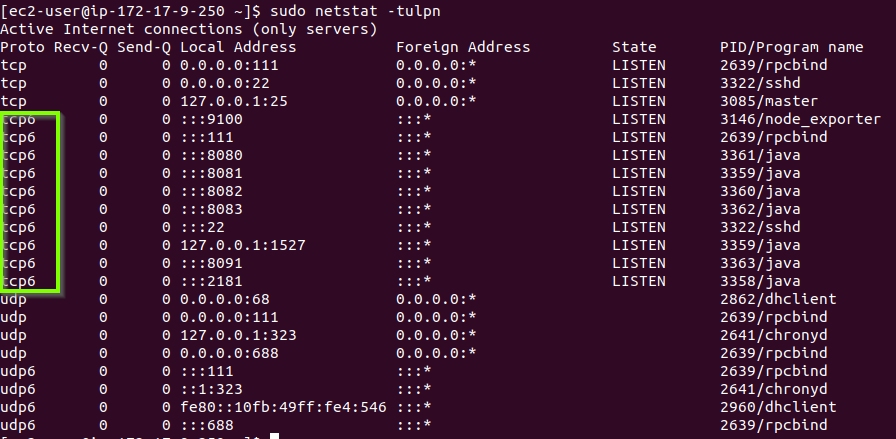
Why netstat shows tcp6 sockets even though you only have ipv4 configured.
The other day I was building an AWS AMI (Amazon Machine Image) with packer which should run some java software. The software itself does not matter.
While testing something I just wanted to check for the ports with netstat. I got this output and was wondering why the ports where of type tcp6. This was in AWS within a VPC which did not have ipv6 enabled.
[ec2-user@ip-172-17-9-250 ~]$ sudo netstat -natp
tcp6 0 0 :::8080 :::* LISTEN 3861/java
tcp6 0 0 :::8082 :::* LISTEN 3860/java
tcp6 0 0 127.0.0.1:1527 :::* LISTEN 3859/java
tcp6 0 0 :::2181 :::* LISTEN 3858/javaI was also able to get a curl running against some web interface from another machine with curl which only had ipv4 enabled as well. That means the application itself was answering on ipv4. Also, I know that ipv4 and ipv6 are not compatible at all. If you wanted ipv4 server to speak with ipv6 and vice versa you need NAT64, which translates ipv4 and ipv6 traffic.
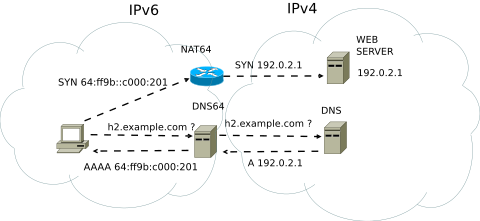
I was confused…
It turns out the socket itself is an ipv6 socket. I also did not know that there is a special ipv6 address range that maps to ipv4 addresses.

That means all ipv4 addresses are also ipv6 addresses.

So these sockets work with ipv4 but since they are really ipv6 sockets they are listed as tcp6 in netstat.
The more you know.